How I found my first Business logic vulnerability — The complete story

بسم الله والصلاة والسلام على رسول الله
It’s my first write-up and first bounty from HackerOne. 😀
Our application is an e-commerce platform (VDP) 🥲, but instead of the traditional approach, they’ve chosen to express their gratitude to me in a more unconventional manner by offering a bounty. 🤑 😂
Today we are gonna talk about logic bug, Not a technical bug actually
→ So focus with me ..
Since it’s an e-commerce platform, I prefer to begin testing its most vital function first (purchasing a product).
Bugs in this function are more likely to be high severity.
One of my favorite scenarios is adding the product to the cart and changing the product price, so let’s try it.
The first step is to add the product to the cart and intercept this request.
After the interception, we detect that the function sends a POST request to this endpoint.

So, let’s take a look at the parameters.

There is one parameter encoded, so let’s decode it and see if there’s any data we can change.
[{"method":"rpc.form","id":9,"params":[{"_SUBMIT":"cart","SKU_BASE_ID":["185285"],"INCREMENT":1,"QTY":1,"_TOKEN":"16efbb7f0a41c7481fabdfc5af81b68d2b214746,3f31ff34f3205b1d90d54b310a815a1dac03c30d,1715797388"}]}]The price is not included in the parameter value. 🥲 But it still may work because there is a ‘QTY’ value that indicates I can add an unpredictable quantity. So, let’s try this way.
[{"method":"rpc.form","id":9,"params":[{"_SUBMIT":"cart","SKU_BASE_ID":["185285"],"INCREMENT":1,"QTY":-1,"_TOKEN":"16efbb7f0a41c7481fabdfc5af81b68d2b214746,3f31ff34f3205b1d90d54b310a815a1dac03c30d,1715797388"}]}]Let’s encode this value and send the request.
There is an error message indicating that validation happens on the quantity value. Let’s try using a fraction number.
[{"method":"rpc.form","id":9,"params":[{"_SUBMIT":"cart","SKU_BASE_ID":["185285"],"INCREMENT":1,"QTY":0.5,"_TOKEN":"16efbb7f0a41c7481fabdfc5af81b68d2b214746,3f31ff34f3205b1d90d54b310a815a1dac03c30d,1715797388"}]}]There is an error message too, so it seems that the add to cart function is secure.
There are different error messages.
The error message for fraction quantity numbers does not originate from the server; instead, it belongs to the endpoint for adding the product to the cart. However, the error for negative quantity numbers is a server error.

Now, let’s check the function for changing the quantity after adding the product to the cart to find another endpoint to send the fraction quantity number to.
First, add the product to the cart, then navigate to the cart page, and intercept the request after changing the quantity of the product.
We detect that the function sends a POST request to this endpoint.
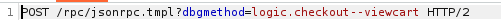
So, let’s take a look at the parameters.

There are two parameters, but since we know JSONRPC has the ‘QTY’ value, let’s decode it and change the ‘QTY’ value to a fraction number.
JSONRPC=[{"method":"logic.checkout--viewcart","id":12,"params":[{"_SUBMIT":"SKU185285_56699009~cart","_TOKEN":"a36ffad611f6c0143f0a86eae2ab3b0094d6fad9,83277beb28395345aaf9e1498b409e6c312fe890,1715813241","QTY":"0.5","SKU_BASE_ID":"185285","CART_ID":"56699009"}]}]
Mission completed!
With 0.5 items and the product price reduced by 50%, it’s evident that there’s a business logic vulnerability in the changing quantity function.

That’s what I’ve got for today’s write-up ..
I hope that I have helped you with any information, even if it is a small one ^_^
That was everything for today’s write-up, Thank you all for reading and for your time ❤
اللهمّ انفعنا بما علّمتنا، وعلّمنا ما ينفعنا، وزدنا علمًا وبارك لنا فيه







